Sales Scam
Sales scams are a type of crime associated with online retailing, where money is snatched from the users without delivering the products. On the other hand, a scammer solicits payment and delivers counterfeit goods. Sales scams are also known as “consumer scams” or “business fraud”. Scammers use a variety of e-commerce fraud methods to commit crimes and fool customers:
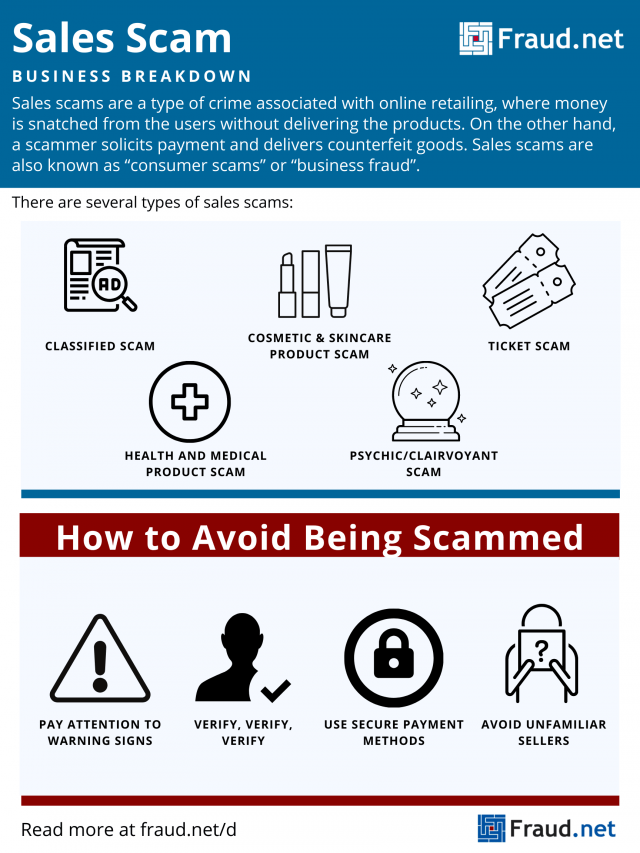
Types of Sales Scams
Classified Scam
In a classified scam, an online retailer lists merchandise on classified websites like Craigslist, eBay, or Backpage without actually possessing that merchandise. A scammer lists photos, details, and “reviews” to fool a customer into purchasing, but steal information from legitimate listings. They often advertise a lower price compared to similar items in that category, further enticing a customer to buy it.
However, once the buyer shows interest, the scammer dodges face-to-face interaction. They claim to have moved and that a friend or agent will deliver following payment. The customer pays, never receives the goods, and cannot contact the seller or the “agent” for a refund.
Scammers take these same steps when listing cars or rental properties, making excuses as to why the customer cannot inspect them. They increase the urgency of the purchase by saying that they’re being deployed or have to leave their property soon. They ask for payments as a “deposit” for interest, but the customer never receives keys to the rental properties or for the car.
Health and Medical Product Scam
This type of fraud takes advantage of both the trustworthiness of health professionals and distrust of common medical practices. In some cases, a scammer builds a fake online pharmacy with listings that resemble legitimate items found at recognizable retailers. On this website, they list wellness products, medicines, and drugs at cheap prices without prescription requirements.
When the customer pays the retailer for these goods, they never deliver them. If the customer does receive the products, they are likely counterfeit and filled with dangerous chemicals that damage their health.
Furthermore, scammers offer “miracle cures”, quick and easy remedies for a health issue or medical condition. These scams weaponize alternative medicine, advertising as cure-alls for serious conditions. They claim to be able to treat AIDS, cancer, the common cold, and many other diseases, but are not backed by reputable doctors or studies.
Scammers deflect criticism by claiming a “medical industry conspiracy” to silence them, and some customers believe them and buy their products. However, these products are usually not proven safe for human consumption, lack reputable research, and interact with current medications, all potentially harming the customer.
Cosmetic and Skincare Product Scam
Scammers list counterfeit cosmetics, often manufactured using cheap and harmful materials, on several online retailers or sell them in street stalls in major cities. They advertise products as reputable legitimate goods, label them with benefits such as “anti-aging”, and sell them at a major discount compared to the real product. Unfortunately, counterfeit products contain cheap or dangerous ingredients like arsenic and cadmium, high levels of abrasive metals, and bacteria from urine or feces. These products cause adverse skin reactions such as eye infections, acne, and rashes. They may also cause various forms of cancer due to the highly carcinogenic materials.
Psychic/Clairvoyant Scam
Most people recognize this type of scam. Scammers claim a customer is in some sort of trouble or “see” a positive event in their future. They offer a solution or help through “winning” lottery numbers, removing a jinx, or offering protection. If the customer refuses to bite, some scammers threaten to invoke a curse or bad luck charm on them. When a customer does pay, the scammer sends them a worthless item or absolutely nothing, or warns of a future event and promises to protect them for ongoing payment. Often, clairvoyant scams lead to a customer being added to a victim list, leading to more scam approaches like lottery or inheritance scams.
Lottery/Sweepstakes Scam
In these, scammers tell victims that they can access lottery winnings or inheritance if they pay a fee. They say a customer has been “selected” as part of a sweepstakes or to use an offer. If they send the message through email or text, they often ask the customer to click a link leading them to a fake web page and pharming their information. Also, that link may be corrupted and make the customer vulnerable to a phishing attack. On the other hand, if they call, they often ask for a credit card or identity information to then use for fraudulent purchases and identity theft.
Auction Scam
Scammers advertise on auction sites like eBay, misrepresenting the product, shipping a low-quality counterfeit, or delivering nothing at all upon sale. They often relist the item with the same information to scam another customer. These scams tend to reap a high reward for scammers due to the nature of online auctions. In addition, foreign auction websites prevent domestic customers from rectifying issues if they don’t receive the product they bid for.
Affiliate Scam
Scammers pose as international companies willing to ship goods to domestic sellers for commerce. They contact individuals, offering a chance to sell high-end items at reduced prices but fail to deliver once the individual makes the sale. Consequently, the buyer at the end of the chain pays for something they never receive, and the seller (if they’re not in on it) loses their reputation and/or profits.
Ticket Scams/Scalping
Scammers advertise tickets to a show whose seats are in high demand or sold out. They sell fake, or “scalped” tickets that often do not work. Scammers may also solicit money from a customer but never deliver tickets.
The variety of sales scams seems daunting, but there are steps customers (and businesses) can take to protect themselves.
Methods to Avoid Sales Scams
Pay Attention to Warning Signs
Scammers use similar methods to commit sales scams - look out for a few signs:
- Listing the product at an unbelievably low price, or advertising amazing benefits and features.
- Insistence on immediate payment or payment through gift cards, money orders, or wiring funds. Scammers want customers to pay quickly and will make excuses as to why they should pay immediately.
- The store is new and selling items at low prices, with limited information about the seller or their policies.
- Retailers that do not provide information about privacy, dispute resolution, or ways to contact.
- Contact information that cannot be verified or is false.
- Resistance to accepting payment through more secure means like credit cards or third-party services like PayPal.
Scam-Specific Warning Signs
- Lottery, sweepstakes, or inheritance scam: insistence on paying upfront to access deals or rewards.
- Health and medical product scam: emails offering pills or treatments that are hard to get or only available through prescription. Moreover, the pharmacy is based overseas or lacks contact information, and/or the product lacks scientific evidence.
- Cosmetic and skincare scams: advertising as "secret formulas" or "breakthroughs", and without any sort of unbiased approval process.
- Classified scams: Sellers who refuse to meet in person or let the buyer physically inspect the merchandise.
- Ticket scams: charging prices much higher than face value. Also, tickets printed with imperfect English or unusual phrases, with the wrong date and time, or with seat numbers or sections that do not exist. Sellers have unverifiable or false addresses, negative reviews, and insist on money orders or gift cards as payment.
Be Proactive
Every time customers shop, they can take a variety of steps to avoid being scammed:
Verify, Verify, Verify
- Verify the identity and contact information of the seller, the product information, and the sales and return policies. Scammers often have addresses or phone numbers that don't exist or don't match their identity, and often have no refund or return policy. If purchasing a used or secondhand item, ask for proof of the original purchase when possible.
- For classifieds, avoid sellers who refuse to meet in person or allow inspection of the product before purchase. If purchasing a vehicle, look up the vehicle identification number (VIN) and the license plate. Look up the name of the last owner to verify, too.
- Avoid doing business with international sellers - these sellers are not beholden to domestic laws if an issue arises. Look up the contents of the product (if purchasing health and wellness products or skincare). Avoid products with ingredients not backed by reputable doctors or studies, or domestically banned.
- If the name of the seller looks like one that you recognize, look up the original seller and verify that they sent you a message. Scammers send emails or promotions that may differ from the legitimate seller's behavior, so keep an eye out for strange wording or behavior. A promotion that the legitimate seller doesn't advertise is most likely a scam.
Use Secure Transaction Methods
- Instead of money or gift cards, money orders, wire transfers, and other forms of payment that are not secure, pay with a credit card. Disputing charges on a credit card is much easier if a customer receives a counterfeit good or nothing at all.
Avoid Unfamiliar Sellers
- When dealing with a new seller, do not make any payments until you verify the seller's identity and reputation. Scam sellers often have little to no reviews or overwhelmingly negative reviews.
- Do not open unfamiliar texts or emails or click links from non-trusted senders. Block unfamiliar senders and do not click on unsubscribe links for clearly fraudulent senders. Clicking the unsubscribe link may be a phishing or pharming ploy.
How Do I Protect My Business?
Fraud.net offers a variety of products to assist with securing online retail sites and preventing fraud. Fraud.net's product offerings are powered by AI and machine learning, to detect and block scammers in real-time. By taking actions to secure online storefronts, fraud becomes less daunting to conquer.
Contact us for a demo or product recommendations today.
SCA (Strong Customer Authentication)
SCA is defined as “an authentication based on the use of two or more elements categorized as knowledge (something only the user knows), possession (something only the user possesses) and inherence (something the user is).The process considers national identity of the customer, tracking of the position, analysis of interest and information of the services. Strong customer authentication is required before any type of business transaction in order to have full access to customer accounts in case of fraud.
Scams
A fraudulent scheme performed by a dishonest individual, group, or company in an attempt to obtain money or something else of value. Scams traditionally resided in confidence tricks, where an individual would misrepresent themselves as someone with skill or authority, i.e. a doctor, lawyer, investor.
Scareware
Malicious software, messages or threats designed to scare people into installing malware and software. A website popup that claims your “computer may be infected with harmful spyware” will send you to a download link for a real malware program.
Scholarship Scam
Scholarship scam is described as a situation where fraudsters offer a fraudulent scholarship to attract the victims. Sometimes the seminars do provide some useful information, but actually they are disguised sales pitches for financial aid consulting services (e.g., maximize your eligibility for financial aid), investment products, scholarship matching services and overpriced student loans.
Scraper
A site scraper can be defined as a kind of software that duplicates content from a website. Site scrapers work similarly to web crawlers, which essentially perform the same function for the purposes of indexing websites. Web crawlers cover the whole Web, however, unlike site scrapers, which target user-specified websites.
Script Kiddie
A script kiddie is an offensive term used to refer to non-serious hackers who use existing computer scripts or code to hack into computers, rather than them creating their own due to them lacking the skills or expertise to write their own.
Second Party Fraud
Second party fraud, or money mules, is where a person allows another to use their identity or personal information to perform fraud. Businesses may find second party fraud difficult to detect and challenge since the identity of the person that is used to carry out fraud has largely allowed it to take place.
Secure Element
A Secure Element (SE) is a microprocessor chip which can store sensitive data and run secure apps such as payment. It acts as a vault, protecting what's inside the SE (applications and data) from malware attacks that are typical in the host (i.e. the device operating system).
Security Protocol
Security protocol, also called cryptographic protocol, could be described as a sequence of operations that ensure the protection of data. Used with a communications protocol, it provides secure delivery of data between two parties.
Security Threat and Risk Assessment
Security Threat and Risk Assessment can be defined as a technique that classifies the overall business and security risks with the aim of defining the competence of security controls, together with the service, in order to reduce the set of risks that appear for the business.
Security token
A security token is a physical device used to gain access to an electronically restricted resource. The token is used in addition to or in place of a password. It acts like an electronic key to access something. Some tokens may store cryptographic keys that may be used to generate a digital signature, or biometric data, such as fingerprint details.
Sensitive data
Sensitive data is defined as information that is protected against unwarranted disclosure. Access to sensitive data must be safeguarded. Protection of sensitive data may be required for legal or ethical reasons, for issues pertaining to personal privacy, or for proprietary considerations.
SEO
SEO is an abbreviation for Search Engine Optimization, which is the art of having your website optimized, or attractive, to the major search engines for optimal indexing. It refers to the process of increasing the quality and quantity of the traffic of the website and this process is used to increase the visibility of web pages for search engine users.
Serious Fraud Office (SFO)
The Serious Fraud Office (SFO) is a non-ministerial government department of the Government of the United Kingdom that investigates and prosecutes serious or complex fraud and corruption in England, Wales and Northern Ireland.
SERP
Search Engine Results Pages (SERP) are the pages displayed by search engines in response to a query by a searcher. The main component of the SERP is the listing of results that are returned by the search engine in response to a keyword query, although the pages may also contain other results such as advertisements.
Shopping Cart
A shopping cart is a feature in online shopping that works as a temporary record of items selected for eventual purchase from the online vendor's website.
Shoulder Surfing
Shoulder surfing is the practice of spying on the user of an ATM, computer, or other electronic device in order to obtain their personal access information. This is generally done by looking over someone's shoulder at the information on screen, hence its name.
SIM Cloning
SIM cloning is the procedure through which a genuine SIM card is reproduced. When the cloning is accomplished, the cloned SIM card’s classifying information is transported onto a separate, secondary SIM card. The secondary card can then be used in a different phone while consuming all the calls and related charges credited to the original SIM card.
Single sign-on
Single sign-on (SSO) is a session and user authentication service that permits a user to use one set of login credentials (e.g., name and password) to access multiple applications. SSO can be used by enterprises, smaller organizations, and individuals to mitigate the management of various usernames and passwords. In a basic web SSO service, an agent module on the application server retrieves the specific authentication credentials for an individual user from a dedicated SSO policy server, while authenticating the user against a user repository such as a lightweight directory access protocol (LDAP). The service authenticates the end user for all the applications the user has been given rights to and eliminates future password prompts for individual applications during the same session.
Skimmer
Skimmers are essentially malicious card readers attached to real payment terminals so that they can harvest data from every person that swipes their cards. The typical ATM skimmer is a small device that fits over an existing card reader.
Skimming
Skimming is considered a type of white-collar crime,and is described as the theft of cash from a business prior to its entry into the accounting system for that company. Although skimming is one of the smallest frauds that can occur, it is also the most difficult to detect.
Skimming cash receipts
Skimming is slang for taking cash "off the top" of the daily receipts of a business (or from any cash transaction involving a third interested party) and officially reporting a lower total. The formal legal term is defalcation. Even though skimming is one of the smallest frauds that could appear, they are considered as the most difficult fraud to detect.
Smart Card
A smart card is a physical card that has an embedded integrated chip that acts as a security token. Smart cards are typically the same size as a driver's license or credit card and can be made out of metal or plastic. They connect to a reader either by direct physical contact (also known as chip and dip) or through a short-range wireless connectivity standard such as radio-frequency identification (RFID) or near-field communication (NFC).
Smurfing/Structuring
The process of laundering money by breaking up large funds into multiple bank accounts to operate under the radar of law enforcement agencies.
In the gaming industry, the term refers to players who create multiple accounts, so that what they do on an alternate account (cheating, losing) will not affect their main account.
Sniffing
Sniffing is the process of monitoring and capturing all data packets passing through given network, and is illegal to be done by an unauthorized party. This stolen information can be used for fraud and obtaining other significant data from users. Sniffers are used by network/system administrators to monitor and troubleshoot network traffic. Attackers use sniffers to capture data packets containing sensitive information such as password, account information etc.
Social Engineering
Psychological manipulation done through human interaction that gets people to reveal personal information for fraudulent purposes. It can happen in one or multiple steps, and can range from basic to complex methods, like attackers impersonating co-workers or officials to solicit information.
Social Media
Social media is a large platform where people entertain, communicate, and connect with the world. It consists of different social networking sites which can be used by hackers and fraudsters to steal personal information of users. This information includes credit card numbers and other personally identifiable information, which are often solicited through "phishing" attacks done on social media sites.
Social Media Intelligence
Social media intelligence refers to the collective tools and solutions that allow organizations to begin conversations, respond to social signals and synthesize social data points into meaningful trends and analysis based on the user's needs.
Social media tracking
Social media tracking or monitoring is a process of using social media channels to track, gather and mine the information and data of certain individuals or groups, usually companies or organizations, to assess their reputation and discern how they are perceived online.
Social Security fraud
Social Security fraud usually occurs when an unauthorized third-party gains access to an individual's Social Security number and exploits it for their own financial benefit.
Social security number (SSN)
A Social Security number (SSN) is a nine-digit number that the U.S. government issues to all U.S. citizens and eligible U.S. residents who apply for one. The government uses this number to keep track of your lifetime earnings and the number of years worked. Using a social security number, personal data can be obtained, and can let a criminal use the information for purposes of defrauding the owner of that social security number. Often this involves stealing money or the identity of that SSN owner.
Software Piracy
Software piracy is the illegal copying, distribution, or use of software. It is such a profitable "business" that it has caught the attention of organized crime groups in a number of countries. According to the Business Software Alliance (BSA), about 36% of all software in current use is stolen.
Spam
Spam refers to an irrelevant or inappropriate message sent on the Internet to a large number of recipients. These messages are often used by scammers to trick people into providing their personal data so that they can be used to blackmail the person. Normally, spam offers an advertisement which is not validated under the actual name of organization.
Spear Phishing
Spear phishing describes when phishing is done with specific targets in mind; this allows messages to these people to appear more legitimate, or as if they are being sent by a legitimate user. For example, a person may get an offer from an organization that he knows. He might click on it and provide confidential information, perhaps to log-in to the website. In reality, the message is not from the actual organization, and he has given his credentials to the actual site to the spear-phisher.
Spider
A spider is a program that visits Web sites and reads their pages and other information in order to create entries for a search engine index. All major search engines on the Web have these kinds of programs, which are also known as "crawlers" or a "bots". Spiders are usually programmed to visit sites that have been marked by their owners as fresh or modernized.
Spoofs
A spoofing attack is when a malicious party impersonates another device or user on a network in order to launch attacks against network hosts, steal data, spread malware or bypass access controls.
Spyware
Spyware is software that can be installed on a computer system or computer device without the device user's knowledge. The software allows the installer to directly obtain or convert information from a computer and to transmit all that data to their own hard drive.
Statute of Limitations
A statute of limitations is a law that sets the maximum time the parties involved have to initiate legal proceedings from the date of an alleged offense, whether civil or criminal. However, cases involving serious crimes, like murder, typically have no maximum period under a statute of limitations.
Stealing
Stealing is the action that occurs when someone takes possession of another person's identity, posessions, or information without any legal rights and without any permission, without any intention of returning it. In computer system the stealing means the unauthorized or illegal copying, sharing or usage of copyright-protected software programs. Software theft may be carried out by individuals, groups or, in some cases, organizations who then distribute the unauthorized software copies to users.
Stealing or providing business secrets
Stealing business secrets is the act of accessing a business's confidential information and revealing it to people who are not properly authorized to see that information. Intellectual property theft is a kind of stealing of business secrets.
STR (Suspicious Transaction Report)
A suspicious transaction report (STR) refers to the information demanded by the Internal Revenue Service (IRS) from banks and other financial institutions regarding suspicious transactions. It provides a report of the financial flows and other information related to the money flows in a regulated private sector.
Supervised Machine Learning
Supervised machine learning is the machine learning task of learning a function that maps an input to an output based on example input-output pairs. It infers a function from labeled training data consisting of a set of training examples.
Sweepstakes Scam
Sweepstakes scams are when a company or fraudster tells someone they have won a sweepstakes prize, but that as the winner they must first pay a fee to insure delivery of their prize. The winner may pay and then never recieve anything.
Sweetheart scam
A sweetheart scam is a situation where a scammer will pretend to be romantically interested in somebody, with the intention of learning their personal information so that they may commit fraud with it.
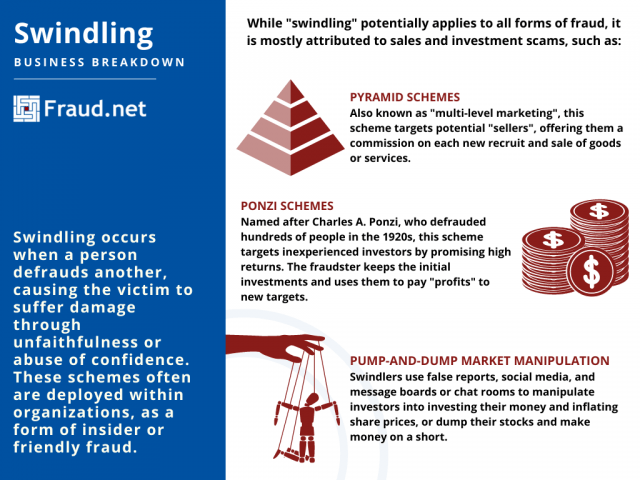
Swindling
The term 'swindler' refers to a person who takes advantage of others through deceit. Swindling occurs when a person defrauds another, causing the victim to suffer damage through unfaithfulness or abuse of confidence. Swindling can be committed by a group of people or individuals involved in defrauding actions to get financial benefits or property by exploitation or fraud. These schemes often are deployed within organizations, as a form of insider or friendly fraud.
While "swindling" potentially applies to all forms of fraud, it is mostly attributed to sales and investment scams, such as:
Ponzi Schemes
Named after Charles A. Ponzi who defrauded hundreds of people in the 1920s, this scam targets inexperienced investors by promising high rates of return. A "promoter" offers to pay an initial investor their principal plus the rate of return, and in order to pay those "returns", targets other investors. Then, more investors become interested because the opportunity seems legitimate and profitable, putting their money into the scheme.
The initial promoter never invests the principal amount, instead siphoning off funds from the investors' initial investments. They pay off "profits" using funds from other investors, and the chain continues until the promoter disappears and the scheme collapses.
Pump-and-Dump Market Manipulation
This scheme is a form of market manipulation, in that the swindler employs this to inflate or deflate prices to earn a profit. Swindlers use false reports, social media, and message boards or chat rooms to manipulate investors into investing their money and inflating share prices, or dump their stocks and make money on a short.
Market manipulation is illegal, and many investors actually lose money in the process.
Pyramid Schemes
In these, the original buyer or swindler obtains the right to enlist others in the "marketing process". This marketing process is most recognizable in beauty product pyramid schemes, in which each seller obtains a supply, and with every buyer and new investor, earns a commission. While this method, also known as "multi-level marketing", isn't technically illegal, the method of recruiting and the language of potential profits mirror those of other swindling schemes. The recruiting method also mirrors that of a Ponzi scheme, in that the most profits come from recruiting new members rather than the product or investment.
These schemes frequently target people in affinity groups (people with shared interests or beliefs), as they often find it easier to recruit investors within these groups.
Fraud.net vs. Swindling
Fraud and swindling are illegal in the US with Title 18 US Code § 1341, which states that those found guilty of fraud are punished with up to 20 years of imprisonment, or a fine of one million dollars. Despite this codification, many businesses choose to mitigate fraud rather than prosecute it. Often, it is easier to mitigate due to the volume of fraud attacks, than prosecute and seek damages.
For this reason, many businesses and institutions employ preventative measures through fraud detection and prevention services. In combination with security best practices training, institutions (and consumers) can avoid being targeted by these schemes or losing money due to dishonest investment recommendations.
Fraud.net offers a wide variety of security solutions to combat money laundering and insider fraud, among other issues. Contact us for a free demo today, and recommendations for fraud prevention.
Synthetic identity
A synthetic identity is created by using a combination of fabricated credentials, leading to a fake identity that is not associated with an actual, real person. Fraudsters may create synthetic identities using potentially valid social security numbers (SSNs) with accompanying false personally identifiable information (PII).
Synthetic Identity Creation
Synthetic Identity Creation (SIC) represent the process of creating a false identity. Synthetic Identity Creation (SIC) as a generic term shows how fraudsters collect information about real people and manipulate their identities with false and fabricated information to ensure the creation of a new identity, which is assigned to no actual real-life person.
System integrator
A systems integrator (or system integrator) is a person or company that specializes in bringing together component subsystems into a whole and ensuring that those subsystems function together, a practice known as system integration. They also solve problems of automation.