Carding
What is carding?
Carding is the general fraudster term for using stolen credit card data, whether it’s used for direct purchases, or charging prepaid or gift store cards, which fraudsters then resell. This particularly targets organizations that handle payment card and transaction processing. One of the greatest threats to your business due to carding fraud are false expense claims, created by authorized staff who reimburse expenses incurred while carrying out their work duties and submit a claim for unqualified reimbursements.
The Open Web Application Security Project outlined the technical criteria that represent this type of fraud. Illicitly obtained payment card data can be validated against a merchant’s payment processing systems. When cybercriminals come into possession of stolen payment card data, the legitimacy is typically unknown. Fraudsters use pre-carding activities such as this to identify valid accounts of high value.
Fraudsters obtain payment card information from several sources:
- Stolen from an application.
- Stolen from a different payment channel.
- Purchased from a criminal marketplace on the dark web.
In some circumstances, criminals only have partial cardholder data at their disposal. For instance, they only have a limited mix or singular instance of expiry dates, security codes, or cardholder names. The subsequent steps taken with partial cardholder data are commonly used in card cracking attempts. From here, the known cardholder data is used to “cash-out” and access cash sums or the purchase of goods.
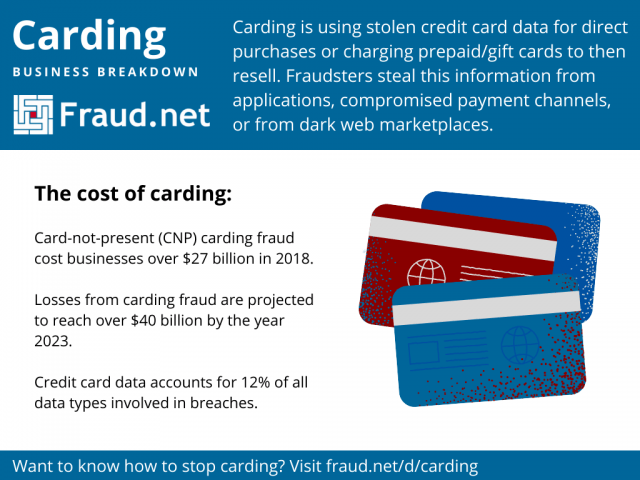
The cost of carding for businesses
Last year, Norton’s LifeLock division reported that “card not present” cases of carding fraud, or remote fraud, cost businesses over $27 billion in 2018. These losses have been projected to reach over $40 billion by the year 2023. As far as customers are concerned, businesses can validate many instances of fraud and offer them a reimbursement for any funds lost. Unfortunately, for institutions that process these payments, there is no recovery available when chargebacks start rolling in.
In the summer of 2021, CreditCards.com published an article highlighting some grim statistics regarding credit card fraud and identity theft. The FTC’s Consumer Sentinel Network 2020 Data Book ranked credit card fraud as the fifth most common type of fraud in the United States. Additionally, credit card information involved in data breaches has persisted at 12% of all data types involved in breaches. This is following the near-doubling of ransomware cases since last year. (Ransomware is a common method for capturing sensitive data and exfiltrating it from a victim’s systems.)
Theft of credit card data is what enables cybercriminals to commit fraud through carding. For example, one common tactic that cybercriminals utilize to move funds and cover their tracks is purchasing gift cards and prepaid debit cards. With stolen funds acquired through carding being filtered through this process, these cards can be resold on the dark web for a discount. Once the cards are sold, cybercriminals obtain untraceable cash hoards using your organization’s money.
Protecting this data is a challenge all its own. However, once this data falls into the wrong hands, organizations that process payment card data are the last line of defense for cardholder accounts. This means leaders need to adopt a proven solution to help prevent carding.
Stop carding with Fraud.net
Fraud.net has responded to the frightening increase in carding fraud by developing a timely solution that leverages artificial intelligence and quality data sources. Transaction AI is built on top of a robust foundation that allows your fraud teams to help combat carding attempts. The Transaction AI solution offers a carding detection capability by employing multiple data points:
- Actionable, real-time alerts of anomalous account behavior.
- Risk scores for every account transaction to reduce false positives for your fraud team, save valuable time and prevent carding attempts sooner.
- Rule-based workflows based on risk that can scale to thousands of instances of carding fraud. The granular definition and governance of these workflows accelerate investigations and can be customized with organization-specific criteria.
Furthermore, Transaction AI places high-value visualizations of fraud trends that you can use to expedite the interpretation and decision-making process. When both large and small volumes of carding attempts are suspected, this allows your fraud teams to remain well-informed of potential criminal activity.
Fraud.net’s powerful platform correlates customer transaction history with billions of unique data points. This data is exclusively provided to Fraud.net customers to give them the extra edge needed to detect carding fraud.
How does Transaction AI work?
Being able to track suspicious activity has never been easier, and reliance on human intuition no longer has to be an obstacle for your organization. Through partnerships with industry vendors and organizations like payment processors, Fraud.net collects transaction data, anonymizes it, and produces real-world case studies on carding fraud.
With this solution, your organization has the necessary tools to rapidly identify carding attempts, no matter which method cybercriminals use.
Stand up and fight carding fraud
Fraud.net is a proven leader in the fight against carding fraud. We can help your fraud teams detect these attempts and disrupt cybercriminals before it’s too late. Protect your business from unwanted scams and a decreased profit margin by signing up for a free fraud analysis today.
Catfishing
A form of social engineering where fraudsters and criminals create fake online identities to lure people into emotional or romantic relationships for personal or financial gain.
Online seduction and blackmail are used to acquire personal information such as credit card numbers, social security numbers, or home addresses, among others.
CC
The fraudster term for stolen credit card data. A full CC contains the original cardholder’s name and address, expiration date, and CCV. It becomes a Fullz when other personal data points are added to the package.
Certified Fraud Examiner
The Certified Fraud Examiner (CFE) is a qualification issued by the Association of Certified Fraud Examiners (ACFE). The ACFE organization is a provider of anti-fraud education and training. CFE training includes teaching about information on difficult financial transactions and appreciating forensic approaches, regulation, and deciding on claims of fraud.
Click Fraud
What is Click Fraud?
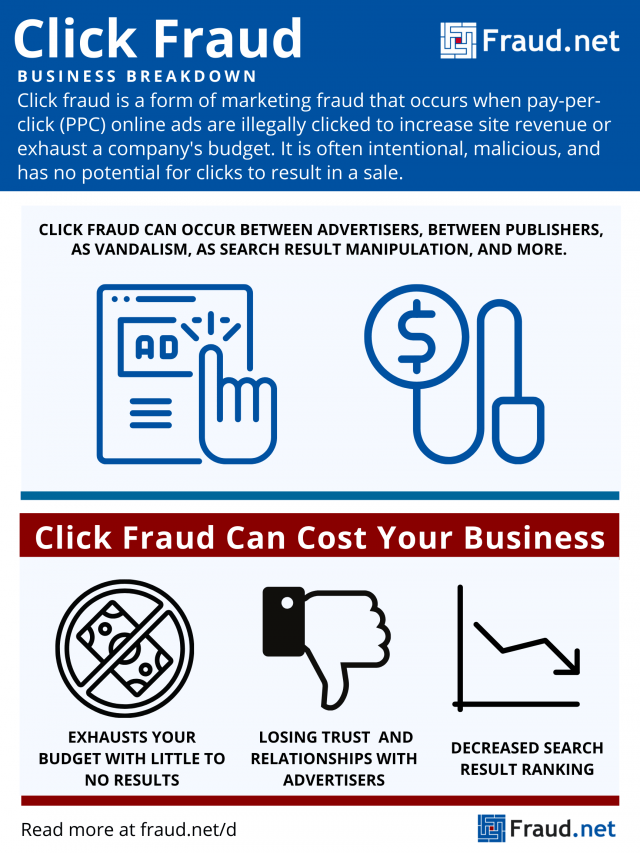
Click fraud is a form of marketing fraud that occurs when pay-per-click (PPC) online ads are illegally clicked to increase site revenue or exhaust a company's budget. It is often intentional, malicious, and has no potential for clicks to result in a sale.
PPC ads generate revenue for publishers or exhaust client budgets for an advertiser based on how much a customer clicks on them (and how many of those clicks are converted to sales). Clicks become fraudulent when those doing the clicking are a computer program (ex. bots), an automated script mimicking a legitimate user or a human with no actual interest in the ad’s target. It is considered a “black hat”, or violating computer security for personal profit or malice.
Sometimes click fraud can be carried out by a site owner to artificially boost ad revenue for their business. It may be carried out by a publisher or ad agency to artificially inflate their click rate making them more appealing to companies looking to market themselves, without actually having such an audience.
Here are several different types:
Non-contracting party click fraud
Between advertisers
One advertiser attempts to use up another advertiser’s budget by engaging in click fraud. Once the latter advertiser’s budget and space are used up on irrelevant clicks, the former becomes the sole advertiser and takes up the space and visibility.
Between publishers
Another version of this occurs when an attacker maliciously attempts to frame a publisher by making it look like they click on their own ads. This would cause an advertiser to mistrust the publisher and end their relationship with them. Because PPC revenue is often the primary source of income, this practice can destroy a publisher’s business.
Vandalism
It is often difficult to track down the culprit of click fraud motivated by vandalism. Often, fraudsters target publishers or advertisers for political or personal vendettas.
Friends and Family
Click fraud can also occur when a publisher is supported by their friends or family clicking on ads to generate revenue. Sometimes the publisher conspires with their personal relationships to commit this type of click fraud, or it is truly just patronage on the part of the friends and family.
Classic click fraud
Site owners (publishers) publish ads using an advertising network like Google AdWords, and click on ads placed on their own sites to increase ad revenue. The advertiser (company creating and placing the ad via advertising network) has their budget exhausted or is defrauded by the actions of the publisher.
Click Farming
Some companies will outsource to low-cost employees to manually click ads all day and generate ad revenue, as part of “click farms”.
Automated Script
A computer program mimics a user and clicks an ad. It does so by translating existing user traffic into clicks and impressions. Another method is to bombard a large number of computers with viruses and have those viruses make the computers click ads.
Hit Inflation
Some advertising publishers use this method to drive traffic from a dishonest site to a dishonest publisher, generating clicks and thus revenue. This occurs when the dishonest site contains a script that converts website interaction on it to clicks for the publisher. The user interacts with the initial site and interacts, not knowing that their interaction is generating clicks for a secondary publisher that they do not directly interact with or are not aware of.
Search Result Manipulation
This iteration of click fraud occurs with the click-through rate of a website rather than PPC ads. Ranking of sites increases when search results generate clicks to those sites - for example, if you were to search “fraud.net” up, the highest clicked site would be listed at the top of search results (that’s us!). In this version, fraudsters generate false clicks on results they want to promote and avoid results they want to demote. The businesses with the higher clicks will have improved rankings while those avoided will not - many malicious publishers or companies will use this to put their competitors at a disadvantage.
The Cost of Click Fraud
According to PPC Protect’s Global PPC Click Fraud Report, 11% of all search clicks are fraudulent, with 17% on connected TV campaigns and 36% on display ad campaigns.
How to Combat Click Fraud
Despite the many ways click fraud can manifest for your business, there are some key things to look out for to check if you’ve been victimized:
- Unusual rises in impressions
- Unusual peaks in clicks
- No corresponding increase in conversions with a click or impression peak
- Page views decrease during click or impression peaks
- High bounce rate during click or impression peaks.
If you suspect you’ve been targeted by click fraud, contact your advertising network running your PPC ads and report your findings. This way, fraudulent clicks can be credited back to your account or budget.
However, the best protection is prevention.
Fraud Prevention with Fraud.net
Fraud.net offers a wide range of products to combat various types of marketing fraud, including click fraud. Contact us for a free demo and product recommendations to protect your business.
Clickjacking
What is Clickjacking?
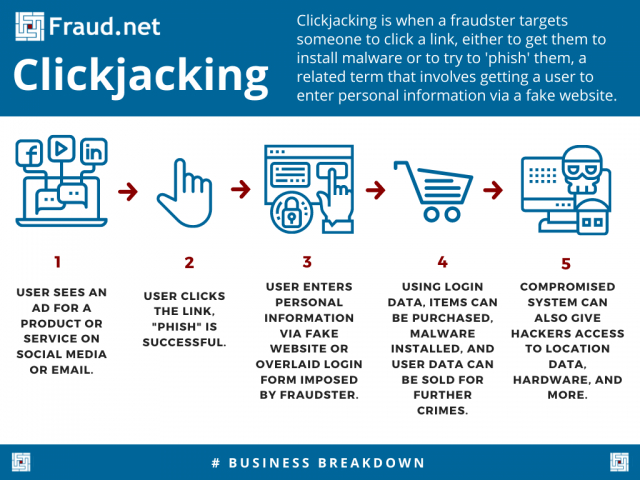
In summary, clickjacking is when a fraudster targets someone to click a link, either to get them to install malware or to try to 'phish' them, a related term that involves getting a user to enter personal information via a fake website.
Clickjacking is done by sharing captivating content that misleads the user. Once people click back to the source of the content, the fraudster then tries to attack them.
What Is There to Gain?
A fraudster has multiple ways to use these clicks for their own gain. With clickjacking, fraudsters can gain access to passwords, credit card numbers and any other valuable data that can be exploited. Clickjacking can also turn features in your devices system on and off when malware is installed. This malware has a lot of capabilities, ranging from enabling microphone and camera access or pulling location data from your device. In short, these clicks can cause strife in the moment, and can make crimes easier in the future.
Clickjacking Examples
A common example of clickjacking involves fraudsters creating a mirror login page to capture user information on a website. With this method, the user assumes that they're entering information into a usual form on a website they visit. In reality, the users can actually be entering that valuable information into an overlaid field controlled by the fraudster. The fraudster gets access without the user ever knowing there was something wrong.
An attacker can also redirect clicks from social media or emails to download malware or gain access to vital systems. This spells trouble for any organizations that rely on protecting sensitive data and intellectual property.
Additionally, links can be hidden under media and trigger a particular action, such as liking a Facebook page or ordering a product on Amazon.
How can Clickjacking be Prevented?
Clickjacking is an intrusive and damaging attack that can lead to serious consequences for you, your customers, and your business. Your company needs a way to proactively stop this attack from turning your website or content into a dangerous environment for users.
A cybersecurity solution like Fraud.net, for example, looks into all methods of fraud, including clickjacking, when securing your site and systems.
Turning fraud prevention into a process that covers the entire customer lifecycle is vital. Whether it comes from leaked data, unauthorized access or payments, and error, Fraud.net will help you find and stop fraudsters of all kinds. Contact Fraud.net for a demo of our end-to-end anti-fraud system, or a free fraud analysis. Start protecting your business today.
Computer Fraud
Computer Fraud is defined as the action of utilizing a computer to attain or modify the electronic information or to get the illegal usage of a mechanical system or computer. Computer fraud in the United States is particularly forbidden by the Computer Fraud and Abuse Act, which specializes in proscribing this matter, which is considered computer-related under the federal authority.
Computer System Penetration
Computer System Penetration, known as a penetration test (or pen test), is an official virtual cyber-attack towards a computer system, executed to assess the security of the system. The test classifies the strengths and weaknesses of the system, as well as how likely it is for someone unauthorized to gain access to the features and data of the system, in order to enable a complete hazard assessment.
Confirmation Fraud
Confirmation fraud is a type of fraud that comes in two layers. First, a fraudster falsifies transactional information, like pretending to deposit a certain amount of money in an account (on someone else's behalf). Then, the fraudster creates fake materials that falsely confirm that that first transaction went through, when in reality it didn't. In short, a fake deposit (or other transaction) is falsely confirmed as having gone through by a fake confirmation, so as to cover up the fact that the first transaction was actually fraudulent.
Conflict of Interest
Conflict of Interest or COI is a situation where a member of multiple interests, in fulfilling their obligations to one interest, can fail the obligations they have to another. The inability to please multiple interests simultaneously, or even just the possibility of not being able to please them both, is then termed a "conflict of interest."
Consumer Authentication
Consumer Authentication is the term used for the devices that are designed to verify that a person making a transaction or any business deal is really the person who is certified to do that action. This term applies to both card-not-present transactions as well as in-person transactions.
Contract Fraud
A person commits contract fraud when they make a knowingly false statement that serves to trick or deceive another person into signing a contract. A person also commits contract fraud when, through misrepresentation, they trick an individual who does not believe they are entering into a contract, into signing one.
Cookie
A "cookie" is defined as a small amount of information that a Web browser saves on the user’s system. Cookies are a method designed for Web applications to retain the application domain. Cookies are commonly used by websites for verification, saving the user's information/preferences on the website, or browsing system information or any other matters that support the Web browser while it gets into the Web servers.
Corporate fraud
Corporate fraud is the purposeful falsification of the financial data of a company or the actions that have been made by the company to deliver fake information to the public, in order to increase the company’s profits. Characteristic cases of corporate fraud are complicated, extremely private, and if exposed consist of the economic indignities and elusions of financial accountabilities that the company has committed.
Corporate Identity Theft
Corporate Identity Theft, also known as CIT, is the deceitful and careful falsification of an identity of a company. It is also sometimes called a “white-collar crime” since it is commonly performed in a “cyber setting,” and is not in the field of the conventional criminal.
Corruption
The term corruption describes when the integrity of an entity is compromised or put at risk by inner actors who aim to illegally or unethically benefit themselves or that entity. The goal of corruption can be financially-related, but does not need to be in order to be considered corruption.
Counterfeit Card
Counterfeit cards are fake credit cards with an actual account's info that can be gained through various methods. A lot of times the victims of these crimes will still have their actual cards and never realize that their information was stolen. These cards might appear to be genuine and even have the issuers’ logos along with the encoded magnetic strips.
Counterfeiting
Counterfeiting is defined as the planned attempt to duplicate a real and authentic article such as a symbol, trademark or even money with the purpose to distort and convince the purchaser or the recipient to believe that he or she is really purchasing or receiving the real article itself.
Crawler
A web crawler, also known as a web spider or web robot, is a program, software package, or automated script which browses the Global Web in a systematic and automated method. Web crawlers are mostly used to generate a duplicate of all the pages they visit, then processing them throughout a search engine that will file the copied pages to deliver faster search results.
Credential Stuffing
Credential stuffing is a form of cyber-attack where a taken account's credentials, usually containing the lists of usernames and/or email ID along with the matching passwords, are stolen and then used to gain illegal access to real user accounts over a large-scale automated login.
Credentials
Credentials refer to achievements or titles bestowed upon someone, generally by an authoritative body, that are brought up in order to validate the capabilities and suitability of that person for a certain task.
Credit Bureau
A credit bureau is an organization that gathers and also investigates the entirity of credit information from a person and then sells the information to the creditors to get a fee so that they will able to make a decision regarding the permitting of a loan. These organizations usually associate with all kinds of loaning institutions and credit issuers to assist them in making any loan decisions.
Credit Card
A credit card is a thin four-sided block of plastic allotted by a financial firm that allows cardholders to borrow some funds to pay for products and services purchases. Credit cards are subject to the condition that cardholders must repay the borrowed cash, sometimes with interest or other charges.
Credit Card Fraud
Credit Card Fraud refers generally to any fraudulent transaction using a credit card as a source of funds. The fraudulent transaction may be committed to obtain goods or services or to illegally obtain funds from an account. Credit card fraud may occur simultaneously with identity theft, but can also occur when a legitimate consumer makes a purchase with no intention of paying for the goods or services, sometimes referred to as chargeback fraud or friendly fraud. Credit card fraud is related to debit card fraud, differing primarily in the form of payment. Another form of credit card fraud is new application fraud, in which a perpetrator applies for a credit card in a victim's name, then uses the card to purchase goods and services illegally. A victim’s credit card information can be acquired in a number of ways, by being purchased on the deep/dark web, by using skimmers at retail points of sale or ATMs, or through corporate data breaches.. The true cost of credit card fraud for merchants is more than just the cost of lost merchandise — it also includes lost profits, bank fees and chargeback costs.
Credit Card Fraud Detection
What is Credit Card Fraud Detection?
Credit card fraud detection refers to the set of policies, tools, methodologies, and practices that credit card companies and financial institutions use to prevent fraudulent purchases, both online and in-store. It involves using various techniques and technologies to identify potentially fraudulent transactions in real-time or post-transaction analysis. The goal is to minimize financial losses for both cardholders and card issuers by quickly identifying and stopping unauthorized or suspicious transactions.
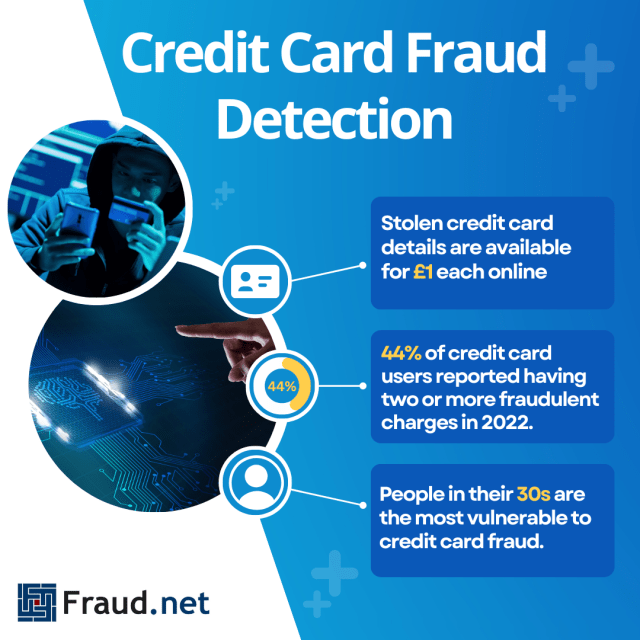
- Stolen credit card details are available for £1 each online
- 44% of credit card users reported having two or more fraudulent charges in 2022.
- People in their 30s are the most vulnerable to credit card fraud.
Common Types of Credit Card Fraud Detection
- Rule-Based Systems: These systems use predefined rules and thresholds to flag transactions that deviate from normal patterns. For example, if a card is used in multiple countries within a short time span, the system might flag it as suspicious.
- Machine Learning (ML) Models: ML algorithms can analyze historical transaction data to identify patterns associated with fraud. These models can learn from new data and adjust their detection techniques accordingly.
- Anomaly Detection: This approach involves identifying transactions that deviate significantly from the expected behavior. Anomalies might include large transactions, transactions in unusual locations, or transactions made at unusual times.
- Behavioral Analysis: This method focuses on understanding the typical spending behavior of a cardholder and flagging transactions that differ from that behavior.
- Geolocation Analysis: By analyzing the geographical location of a transaction and comparing it to the cardholder's usual locations, fraud detection systems can identify suspicious transactions.
How It's Different from Similar Fraud Detection
Credit card fraud detection has unique characteristics due to the nature of credit card transactions. Unlike other types of fraud detection, it:
- Focuses on financial transactions, especially electronic payments.
- Involves real-time monitoring to prevent immediate financial loss.
- Utilizes behavioral patterns and transaction history specific to individual cardholders.
- Needs to balance between minimizing false positives (legitimate transactions flagged as fraud) and false negatives (fraudulent transactions not detected).
It specifically focuses on preventing fraudulent purchases made using credit cards. It differs from other types of fraud detection, such as insurance fraud detection or healthcare fraud detection, which focuses on preventing fraudulent claims or transactions in those specific industries.
Solutions for Credit Card Fraud
Credit card fraud detection employs a multifaceted approach to safeguard financial transactions. Machine learning algorithms, including neural networks, decision trees, and ensemble methods, are adept at learning from historical transaction data to recognize fraud-related patterns. Predictive analytics harness historical data and statistical techniques to gauge the likelihood of a transaction being fraudulent. Real-time monitoring systems swiftly identify and thwart fraudulent activities as they unfold, ensuring prompt intervention.
Furthermore, biometric authentication offers an additional layer of security by utilizing traits like fingerprints and facial recognition, thereby mitigating the risk of unauthorized transactions. Behavioral analytics delves into spending habits, transaction frequencies, and behavioral trends to pinpoint irregular activities. Augmenting transaction data with external information, such as device data and geolocation, through data enrichment techniques, enhances the accuracy of fraud identification. This comprehensive arsenal of methods collaborates to fortify credit card fraud management, providing a dynamic defense against evolving fraudulent tactics.
For instance, a machine learning model trained on a dataset of legitimate and fraudulent transactions can learn to differentiate between normal spending patterns and unusual activities. Let's say a user typically makes transactions within a certain geographic region and at specific times of the day. If suddenly, there are multiple transactions from different countries or during unusual hours, the machine learning model can flag these transactions as potentially fraudulent.
Don't Wait for Fraud: Take Charge of Your Security Against Credit Card Scams!
Fraud.net offers a comprehensive fraud detection solution that combines machine learning algorithms, behavioral analytics, and real-time monitoring. It employs advanced algorithms to detect anomalies and suspicious behavior, helping businesses prevent credit card fraud. Book a meeting today to learn more about how Fraud.net's solution can help your specific needs!
Credit Card Number
A credit card number is the exclusive number printed on a credit card. The first six numbers written on a credit card are the issuer's identification numbers, and the last remaining numbers are exclusive to the specific card. These credit card numbers are typically available in embossed form on the credit card.
Credit Card Refund Schemes
What are Credit Card Refund Schemes?
Credit card refund schemes are fraudulent activities in which scammers exploit the refund process of credit card transactions to illegitimately obtain money or goods. In refund schemes, fraudsters employ clever strategies to obtain money or items that they shouldn’t rightfully have. They engage in deceptive tactics to manipulate the way refunds are processed. This allows them to receive money that they have no legitimate claim to.
Credit card refund schemes can lead to financial losses for businesses, financial institutions, and individuals.
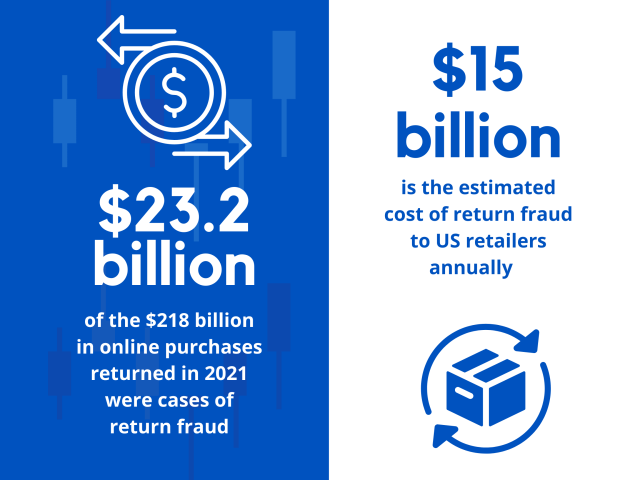
- Approximately $23.2 billion of the $218 billion in online purchases returned in 2021 were cases of return fraud
- Return fraud is estimated to cost US retailers over $15 billion in losses annually
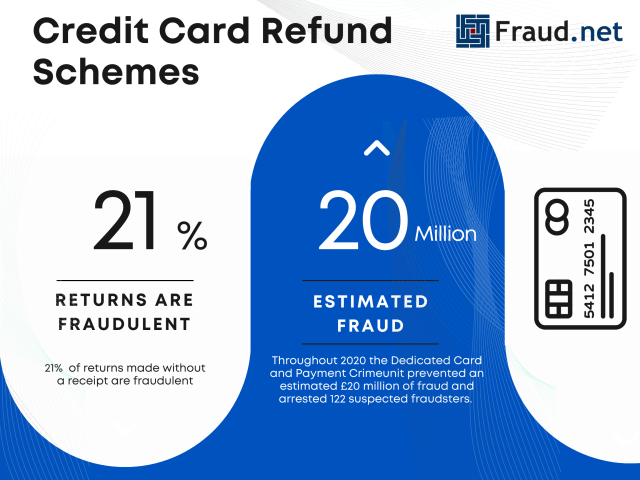
- 21% of returns made without a receipt are fraudulent
- The Dedicated Card and Payment Crime Unit protected an estimated £20 million from potential refund schemes and arrested 122 suspected fraudsters.
Common types of credit card refund schemes:
- Return Fraud: A fraudster purchases items using a credit card and then returns them for a refund, often claiming the items were defective or not received, even though they were never purchased.
- Overpayment Refund Fraud: The fraudster makes a larger payment than necessary and then requests a refund for the overpayment amount.
- Virtual Item Fraud: In online transactions, a fraudster may purchase virtual goods or services, claim they were never received, and request a refund.
- Collusion with Employees: Fraudsters collude with employees to process fake refunds and share the proceeds.
Credit card refund schemes differ from legitimate refund processes by involving deception or manipulation to obtain refunds that are not justified. Legitimate refunds are intended to rectify genuine errors or customer dissatisfaction.
Solutions for Refund Fraud
Mitigating credit card refund schemes involves a combination of strategies:
- Transaction Monitoring: Implement advanced analytics to detect patterns indicative of refund fraud, such as multiple refunds for the same item or excessive refund requests.
- Documentation Verification: Require detailed documentation for refund requests, including proof of purchase and reasons for the refund.
- Automated Fraud Detection: Utilize automated systems to cross-reference refund requests with historical transaction data and flag anomalies.
- Employee Training: Educate employees about common refund fraud tactics and how to identify suspicious refund requests.
- Refund Approval Process: Institute a multi-level approval process for refunds that involve high amounts or deviate from regular patterns.
- Customer Authentication: Implement strong customer authentication methods to verify the identity of the person requesting the refund.
- Data Sharing: Collaborate with industry partners and organizations to share information about known refund fraudsters and patterns.
Fraud.net’s Solution
Fraud.net offers an advanced fraud prevention solution with features tailored to combat credit card refund schemes:
Pattern Recognition, a crucial component, harnesses the capabilities of machine learning. By scrutinizing refund patterns and behaviors, this technology helps identify deviations that might suggest fraudulent activities. Transaction Analysis delves into historical transaction data. Its role is to meticulously sift through this data, aiming to uncover any irregularities or anomalies present within refund requests. This systematic examination contributes significantly to detecting suspicious activities and potential fraud.
Customer Verification stands as a pivotal safeguard in the refund ecosystem. It provides essential tools that enable organizations to verify the identities of their customers. This step is essential to ensure that refunds are direc
ted to the rightful recipients, preventing any illegitimate diversion of funds. The advantage of Real-time Monitoring cannot be overstated. It acts as a vigilant guardian, capable of issuing instant alerts when any suspicious refund activities are detected. This real-time notification system empowers organizations to intervene swiftly and prevent any further potential harm. Lastly, the importance of Industry Collaboration cannot be overlooked. A collective defense is established against evolving refund fraud tactics by fostering information sharing among different entities. This collaborative approach ensures that knowledge is pooled, enabling organizations to proactively adapt and counter emerging threats effectively.
We invite you to request a demo or consultation with our experts to explore how Fraud.net’s comprehensive fraud prevention solution can safeguard your business against credit card refund schemes and other fraudulent activities. Take proactive steps to protect your business’s financial integrity today.
Credit Fraud
Credit fraud is described as a situation where a customer's personal information has been stolen by a fraudster in order to make a new credit claim using the stolen information. In this case, the customer's name may not be authorized.
Cryptocurrency
A cryptocurrency is a virtual or digital currency that applies cryptography for safety purposes. A crypto currency is quite challenging to counterfeit because of the security feature. Many of the crypto currencies are distributed systems built on Blockchain technology, which is a scattered accounting book applied by a dissimilar system of computers.
Cryptogram
A cryptogram is a form of puzzle that contains a small part of encrypted text. Usually the code used to encrypt the text is quite simple so that the cryptogram can be resolved manually. Often the cryptogram is used for exchange codes where each letter is exchanged for a different number or letter.
Cryptography
Cryptography is the study (as well as the practice) of methods for secure communication in the presence of malicious third parties. Generally, cryptography is centered around creating and investigating procedures that prevent the public from reading confidential messages. A number of data security features such as data privacy, data truthfulness, verification, and even non-refutation are essential for contemporary cryptography.
Cryptomining
Cryptocurrencies require large amounts of computer power to be created, or “mined”. Some legitimate companies specialize in mass cryptomining through dedicated mining farms.
Cyber criminals and fraudsters, however, like to deploy cryptomining viruses or bots on unsuspecting users’ computers, or even organizations’ servers. This allows them to mine at scale, without spending extra money on equipment or resources like electricity.
Current Address Fraud
Current address fraud occurs when a fraudster changes the known address of somebody to a new one, thus re-routing their mail to somewhere the fraudster can likely access it.
Customer Due Diligence
Customer Due Diligence, also known as CDD, is defined as the method by which appropriate data or information regarding the customer is gathered as well as assessed for any possible threat for the business, money laundering, or even terrorist financing actions.
Customer Identity and Access Management
Customer Identity and Access Management, also known as CIAM, could be defined as a subsection of the broader Identity Access Management or IAM, and it specifically focuses on dealing with or handling personalities, access, and the security designed for software applications.
CVV (Card Verification Value)
What is a CVV?
The card verification value (CVV), is a three- or four-digit code on the back of a debit or credit card. It is sometimes referred to as a CID, or card identification number. This unique code is used to verify that a shopper has physical access to the card they’re using to pay for goods or services. Other qualities of a card can be stolen or copied through methods like using a card skimmer, but the CVV won't be recorded through those methods, making the CVV a useful and important authenticator in online card transactions.
Why do merchants ask for a CVV?
When paying online or via phone, merchants request the CVV to check whether it matches the information from the issuing bank. Banks and credit card companies use advanced algorithms that are impossible to spoof to generate CVVs. They are based on information like the account number or expiration date of the card.
Asking for the CVV during checkout protects merchants and consumers from card-not-present fraud. This fraud is on the rise. In fact, payment fraud involving credit cards amounts to $100 billion in losses each year globally.
How to protect your card verification value
Preventing your CVV from falling into the wrong hands protects you from criminals making unauthorized transactions with your card.
Even though data breaches are a major concern, the risk of hackers stealing CVV numbers during breaches is very low since PCI standards specify that merchants shouldn't store CVVs once a transaction is completed.
Merchants can even process recurring payments without a CVV once they obtain the proper authorization from the user to avoid storing this sensitive information.
Nonetheless, consumers should be aware of a few things in order to protect their card verification value and other information:
- Phishing is a common way of stealing payment credentials. With three billion phishing emails sent daily, it pays to be wary of any email requests to share payment details.
- Phishing isn’t limited to emails. Some scammers use sophisticated social engineering schemes that involve calling victims to trick them into sharing sensitive payment information. Don't do it. Credit card companies won't ask for this information over the phone.
- Malware such as keyloggers can spy on a user and record everything they type online, including credit card numbers, before sending this information back to a hacker.
Protect Your Business with Fraud.net
As a business owner, you can protect your organization from phishing with an email shield.
Fraud.net’s Email AI solution can analyze multiple data points to spot malicious emails and alert users that a message could contain malware or come from a criminal phishing for payment credentials.
Contact us today for a free demo and product recommendations.
Cyber Fraud
Cyber fraud is described as a situation in which a fraudster uses the Internet to earn money, products, or some other interest on things which they obtained illegally from people, generally through deceiving or tricking them.