Tax Identity Theft
The term "tax identity theft" represents fraud made by someone to get advantages in tax returns and tax payments. Tax-related identity theft occurs when someone uses your stolen Social Security Number to file a tax return claiming a fraudulent refund. People create false identity by using the personal information of another person to demand a fraudulent tax return. The only way to detect this kind of fraud is a notice from IRS (The Internal Revenue Service).
Tech Support Scams
A technical support scam refers to a type of telephone fraud, where a scammer claims to be able to provide a legitimate technical support service, frequently through cold calls to innocent users, with the hopes of eliciting a payment without completing the services requested. These calls are mostly targeted at Microsoft Windows users, with the caller often claiming to represent a Microsoft technical support department.
Technology Theft
High technology crimes (or cybercrimes) are generally defined as any type of illegal activity that makes use of the internet, a private or public network, or an in-house computer system. Technology theft can be described as a scheme where different activities are conducted by one or more thieves, in order to steal techniques, resources, or devices, with the aim of obtaining personal benefits from those actions.
Telecommunication fraud
Telecommunication fraud is the theft of telecommunication services (such astelephones, cell phones, computers and so on) or the use of telecommunication service to commit other forms of fraud. Victims of the fraud include consumers, businesses and communication service providers.
Telecommunications
Telecommunications refers to the exchange of information by electronic and electrical means over a significant distance. A complete telecommunication arrangement is made up of two or more stations equipped with transmitter and receiver devices.
Theft of Assets
Theft of assets refers to the actual theft of a person or entity's assets. Causing an organization to pay for goods and services not actually received (for example fictitious vendors or employees) or using an organization's assets for personal use are types of theft of assets.
Theft of Checks
Check theft involves stealing, and usually cashing, the check of another. Check theft may also refer to receiving goods or services by passing a bad check which is noncollectable due to insufficient funds or closed account. Penalties for this fraud vary by state.
Threat
A threat is any condition or event that may negatively influence managerial operations (include assignment, purpose, picture, or status), organizational resources, or individuals through an information scheme by using illegal access, devastation, confession, alteration of information, and/or rejection of service.
Timecard Tampering
Timecard Tampering, also known as time sheet or time card fraud, is when an employee puts down hours they did not work and collects payment for them. There are rules and laws in place against it but some employees still try to game the system to get more pay and commit time theft.
Token
A token is a unique frame that is approved from node to node about a ring system, it is a sequence of bits passed continuously between nodes in a fixed order and enables a node to transmit information. When it gets to a node that requires transmitting data, the node modifies the token into a data frame and transfers it to the receiver. A token is fundamental to the internal workings of a token ring network.
Tokenization
Tokenization is the process of replacing sensitive data with unique identification symbols that retain all the essential information about the data without compromising its security. Tokenization, which seeks to minimize the amount of data a business needs to keep on hand, has become a popular way for small and mid-sized businesses to bolster the security of credit card and e-commerce transactions while minimizing the cost and complexity of compliance with industry standards and government regulations.
TOR
TOR is a free and open-source software that allows anonymous web surfing and protecting against traffic analysis. The name comes from an acronym for a software project named "The Onion Router." The browser uses exit relays and encrypted tunnels to hide user traffic within the network.
Transaction Authentication Number (TAN)
A transaction authentication number (TAN) is a one-time use code involved in processing online transactions. It offers additional security on top of a password to log in to an account or make transactions. To decrease chances of fraud in transactions, some companies may require a TAN as a form of multi-factor authentication (MFA), in addition to a PIN number or CVV. New TANs may be provided with each interaction, or a list of trusted TANs may be provided to an individual that they can choose from when conducting business.
If the document or token containing a TAN is stolen, it is useless without the original password. Conversely, if one logged in without a valid TAN, they would not be able to gain access.
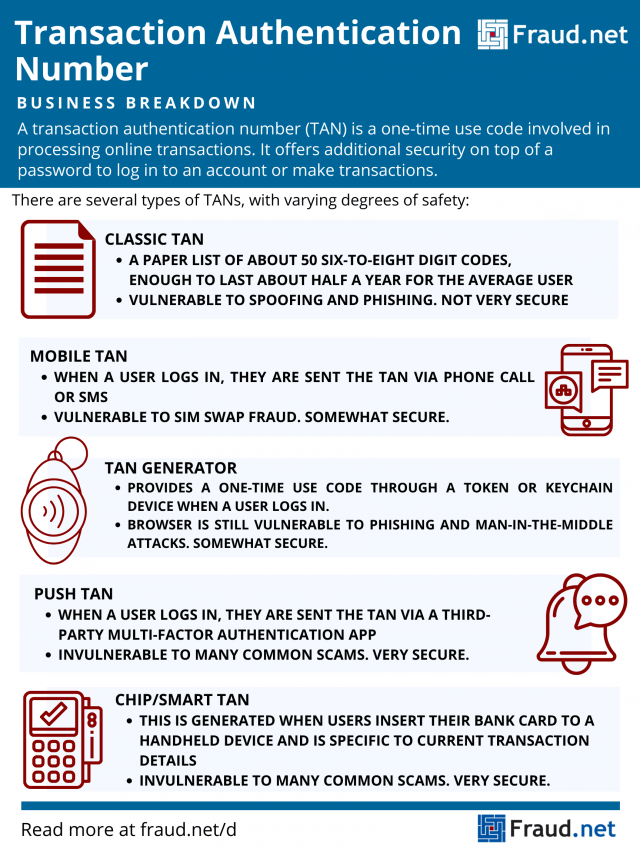
Types of Transaction Authentication Numbers
Institutions offer a variety of forms of delivering TANs to users. Each institution has its own preference based on what it requires and what its users desire. Below are several types of TANs, and the vulnerabilities they each have.
Classic TAN
Financial institutions provide a list of about 50 TANs, usually enough to last about half a year for each user. These TANs comprise of six- to eight-digit unique codes for a user to enter to verify online transaction activity and identity. Users obtain this list at their financial institution or receive it by mail, separate from their login credentials. When a user logs into their account and verifies a transaction, the TAN they use becomes defunct and unusable for future transactions. If someone steals a TAN list or disposes of it by accident, the user can obtain a new list from their institution. All codes on the old list are unusable for that particular user.
Unfortunately, scammers successfully engage in phishing attacks with these TANs. A scammer prompts users to enter both their PIN and TAN (or several TANs) into fraudulent login pages. They then use those credentials to authorize fraudulent transactions. Further, TANS provide little to no protection against man-in-the-middle attacks (MitM). In these, scammers intercept the TAN and use it for their own purposes, especially in compromised or vulnerable systems.
Indexed TAN (iTAN) and iTAN with CAPTCHA (iTANplus)
Users enter a specific tan identified with a sequence number, or "index". These are randomly chosen by the bank, so if a scammer obtains a TAN, it is worthless without the index. However, scammers are still able to conduct MitM attacks, including phishing and man-in-the-browser (MitB) attacks. Scammers conduct these attacks by swapping transaction details in the background and concealing fraudulent transactions in account overviews.
Some organizations combat this with the use of CAPTCHA. Users complete a challenge before, after, or during entry of their TAN. If they cannot complete it, the page denies access. CAPTCHA provides further protection through embedding transaction information, so scammers spoofing this would have their transactions flagged. Despite added protection, scammers still successfully conduct automated attacks like distributed denial-of-service (DDoS).
Mobile TAN (mTAN)
These TANs are more recognizable to common users than TAN lists. Users conducting transactions enter a code sent by SMS or phone call to access the service and verify transactions. Sometimes, the SMS itself includes transaction data so users can verify details before the transaction transmits to the bank.
This form of authentication is also vulnerable to fraud. Scammers use SIM Swap Fraud to obtain TAN numbers for fraudulent transactions. In SIM Swap, scammers impersonate victims, asking for replacement SIMs from their network operator. When the scammer logs in using the user's credentials, obtained through other means, they receive the TAN message and gain access to the account. The victim often realizes too late, when they discover their phone has stopped working or see their accounts compromised.
Further, as smartphones act as mobile computers, attackers can more easily attack both the computer and phone. This leaves them both vulnerable to spoofing and phishing attempts.
TAN Generators
These provide a one-time use code through a token or keychain device. The token displays the TAN after a user logs in, or when a smart card is inserted. Unfortunately, these TANs do not contain specific transaction details, so scammers easily conduct phishing and MitM attacks.
pushTAN
Similarly to mTAN, when users log in to their accounts, they receive a single-use TAN from a third-party multi-factor authentication app like Duo Mobile. It does not incur text message charges. Therefore, it protects against SIM Swap Fraud, since messages are encrypted and do not rely on phone numbers. As an added precaution, the pushTAN app stops functioning if it detects a "rooted" or jailbroken phone.
ChipTAN/SmartTAN/CardTAN
One of the strongest forms of TAN generation, this type of TAN is generated when users insert their bank card into a handheld device. Each generated TAN is specific to that bank card and current transaction details. Nowadays, these devices generate TANs through verification of a flashing barcode on the computer screen. Users must then confirm the transaction on their TAN device.
Because the generator consists of independent hardware provided by tech companies and banks, this method protects against computer attacks. The generated TAN works only for transactions confirmed by the user on the generator screen itself. Furthermore, in case of device loss or theft, users can request new ones without worrying about fraud - specific TANs can only be obtained with a bank card. Despite added protections, scammers successfully persuade users to authorize "test transfers" or "return of falsely transferred money", posing as a bank or company.
How Do I Prevent Banking Fraud?
Despite the added security of TANs, businesses and financial institutions commonly find themselves vulnerable to banking fraud attempts. To protect customers and institutions, implementing the strongest TAN methods and cybersecurity solutions will only prove beneficial.
Fraud.net offers a variety of cybersecurity solutions specifically engineered to protect commercial and financial institutions. Our products, powered by artificial intelligence and machine learning, keep your systems protected from phishing and spoofing attacks. With the automation that AI and machine learning provide, these products evolve with you, learning from previous attacks to suit your needs down the line. By protecting your transactions, you protect your customers, your business, and your bottom line.
To learn more about Fraud.net's product offerings and request a demo, contact us today.
Triangulation Fraud
What is Triangulation Fraud?
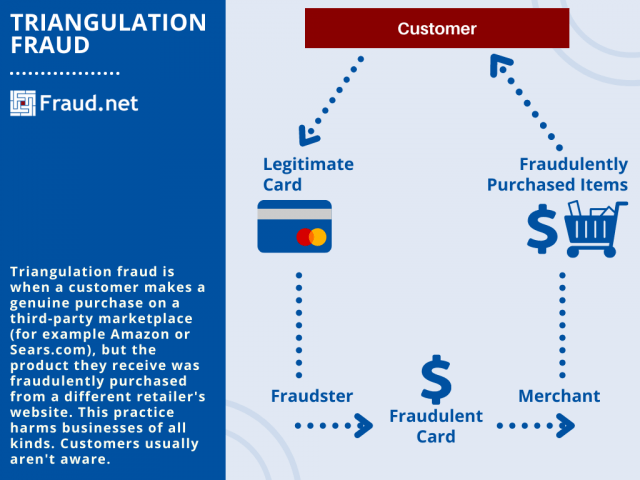
Triangulation fraud is when a customer makes a genuine purchase on a third-party marketplace (for example Amazon or Sears.com), but the product they receive was fraudulently purchased from a different retailer's website. This practice harms businesses of all kinds. Customers usually aren't aware.
Triangulation fraud denotes that there are three individuals who play a role in the order.
- An unsuspecting customer who places an order on an auction or marketplace using some form of credit, debit, or PayPal tender.
- A fraudulent seller who receives that order and then places the order for the actual product with a legitimate eCommerce website using a stolen credit card.
- A legitimate eCommerce website that then processes the criminal’s order.
The illegitimate purchase is made using stolen card information from someone else, but the shipping information of the original customer. So the customer is shipped the product, and fraudster keeps his money. Meanwhile, the fraudster charges the legitimate retailer with other credit card information, further boosting net profit.
Often, the person with the stolen credit card details will dispute this charge, causing the original retailer to refund the purchase. The customer at the beginning of the transaction has no idea. Consequently, the fraudster in the middle wins big.
The Costs
These chargebacks indefinitely hurt the merchant most. Studies show that these fraudsters will cost merchants upwards of $30 billion a year by 2020. Even at the scale of medium to small size businesses, the losses can be detrimental. A brief look at any third party marketplace forum will show hundreds of disputed transactions and mystified sellers. These losses can add up to hundreds of thousands of dollars for even the smallest enterprises. The numbers will continue to grow with the rise of eCommerce.
Protect Your Business
However, triangulation Fraud can be stopped. Address and location verification that matches the customer are just some examples of how Fraud.net's software combats fraud. With insights from user behavior, location, and fraud scoring, Fraud.net can stop transactions in place. Advanced AI technology keeps an eye on fraudsters, card information, and more. Dark web monitoring and continuous testing allow fraud prevention to develop with the fraudsters.
Above all, eCommerce will only expand. And so should your solution. With a powerful portfolio of solutions, Fraud.net can meet your unique needs to quickly and cost-effectively. Contact us for a free demo.
Trojan
A trojan, or trojan horse virus, is a computer program that seems legitimate, but adds malware to a device once downloaded. It’s name comes from a famous Greek tale.
True Negative
True negative, also known as specificity, is the ratio of correctly identified non-fraud cases to total non-fraud cases. A true negative test result is one that does not detect the condition when the condition is absent. It is an outcome where the model correctly predicts the negative class, for example if a disease test correctly identifies a healthy person as not having that disease.
True Positive
A “true positive” occurs when something innocent is wrongly deemed suspicious. Card issuers have developed sophisticated, automated fraud detection systems that work by detecting activities and patterns associated with fraud, but these systems don't work perfectly.This differs from false positives, which are negative results that a system incorrectly marks as positive.
Trust
A trust is a fiduciary connection where one person places some type of trust, confidence, or reliance on another person. The person who is delegated that trust and confidence would then have a fiduciary duty to act for the benefit and interest of the other party. The party who owes a duty to act for the best interest of the other party is called the fiduciary. The party to whom the duty is owed are called principal. The main purpose for fiduciary connection is to establish an honest and trusted relationship between two parties where one party can rely and be confident that the other person is working for their interest and are not using their power for their own interest or the interest of a third party.
Trusted Third-Party
In cryptography, a Trusted Third-Party (TTP) is an entity which facilitates interactions between two parties who both trust the third party; the Third Party reviews all the critical transaction communications between the parties. TTPs are ordinary in profitable transactions, cryptographic digital transactions, and in cryptographic protocols.
Two tier affiliate program
In a two-tier affiliate program, or a multi-tier program (two or more levels), the first tier of commission is the same as in a regular affiliate program. The only difference is the additional tier(s), whereby marketers also earn a commission on sales generated by people they referred to the program.
Two-Factor Authentication (2FA)
2FA or Two-Factor Authentication, also called Step-Up Authentication, is a security process in which the user provides two means of identification, one of which is typically a physical token, such as a card, and the other of which is typically something memorized, such as a security code. Two-Factor Authentication gives users an extra layer of security when accessing their online accounts. In addition to a typical combination of username and password, a second 'factor' is added, such as a numeric code displayed on a trusted device, to heighten the certainty that you are the one attempting to access your account. 2FA is a method of determining a user's identity by confirming two factors among 1) something the user knows (i.e. mother's maiden name), 2) something the user has (i.e. mobile phone) and 3) something the user is (i.e fingerprint). 2FA is a subset of the broader multi-factor authentication (MFA).
Fraud.net offers Two-Factor Authentication as a feature within our Fraud Prevention Suite.
Here's how it works:
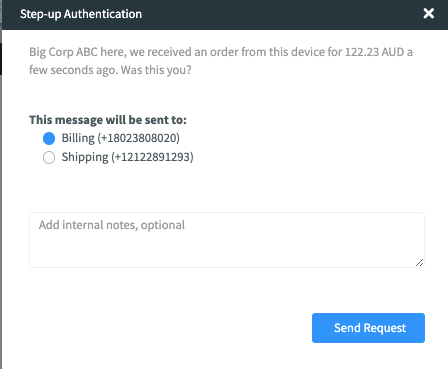
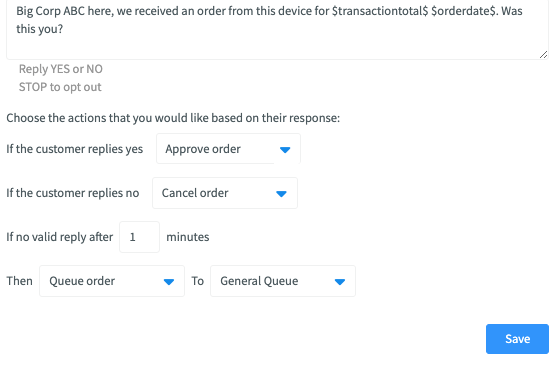
Fraud.net's 2FA feature gives fraud analysts the ability to send a verification text message to the phone number of a transaction. The purpose of this is to authenticate that the phone number within the transaction is owned by the person who actually placed the transaction. A Yes/No question will be sent to a phone and then based on the response the transaction, it can be auto-cancelled, auto-approved or sent to a queue for further review.
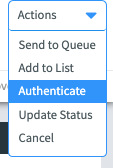
1. When a fraud analyst is reviewing a transaction, they can select the option to authenticate the transaction (Send MFA) from the dropdown menu in the top right corner:
2. The fraud analyst will then confirm that they would like that message sent:
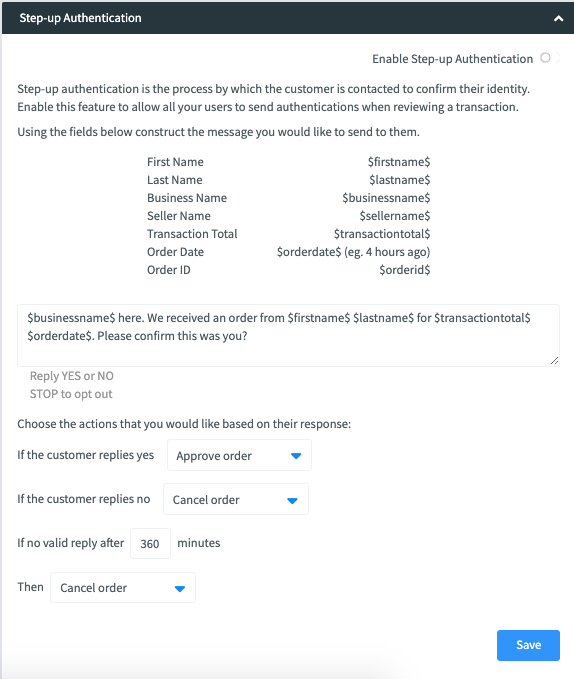
3. The admin, from the business profile page, can manage what the message says and what action occurs based on the reply. The admin can also manage what happens when no reply is received and the time frame for the reply. The default question reads as "$business name$ here. We received a transaction from $firstname$ $lastname$ for $amount$ on $orderdate$. Was this you?"
Reply Yes or No"
4. The transaction remains in a pending authentication queue until there is a response or it expires.