A/B testing
A/B testing is a research method in which two groups, a control group (representing the current strategy) and an alternate group (representing a hypothesis for an improved strategy), are tested against one another in order to scientifically select the optimal final strategy.
Account Takeover Fraud (ATO)
ATO Fraud or Account Takeover Fraud is a form of identity theft in which a criminal gains control of a consumer’s account. In doing so, the perpetrator gains access to confidential information amongst the type of account, such as the consumer’s PIN, enabling them to change account settings, such as the statement mailing address, username and password, and/or enabling them to make unauthorized withdrawals.
ATO can involve one or multiple accounts of the victim — including, but limited to, bank account, email address, brokerage, phone, utility, social media, travel or online shopping accounts — and then used for a variety of unlawful activities with their personal information. Financial account takeover usually involves funds being removed from the victim’s accounts either by direct debit, payments or transfers being set up for fraudulent transactions without the victim’s knowledge or consent.
How Criminals Attempt Account Takeover Fraud
With account takeover of mobile phones, often the perpetrator’s intent is to gain control of the phone-based security authentication factor through a login attempt, which is usually a code or security token sent via SMS or authentication software to the phone. Once it is acquired by the criminal, the code can grant him/her access to the victim’s financial institution, brokerage, bitcoin and other financial accounts.
The credentials to commit account takeover are usually obtained by criminals indirectly through data breach marketplaces on the dark web or directly from the consumer using malware or via phishing. Once a fraudster gains access to a victim’s account, they often update the account credentials and contact information so the victim no longer no has control over the account and will no longer be informed about changes to the account. In most cases, the victims are unaware that their account has been compromised until the damage is done and the perpetrators have covered their tracks.
Fraud.net Has a Solution
To protect against Account Takeover Fraud, Fraud.net offers a variety of solutions to protect your business. With the power of AI and machine learning, our solutions help stop fraud in its tracks - before it destroys your company.
Contact us today for a free demo and recommendations.
Acquirer (Acquiring Bank)
The Acquiring Bank, also known as the merchant acquirer or the merchant bank, is the bank that is responsible for settling credit and debit card transactions on behalf of the merchant. Its counterpart is the issuing bank which settles card transactions for the purchaser or card holder. Acquirers enable merchants to accept credit cards, often provide merchants with necessary hardware and software to accept card transactions, and for their role in the card payment process, receive an acquirer fee or markup in addition to the interchange and other fees in a credit card and debit card payment.
Active Authentication
Active Authentication is a security and authentication method in which the user is challenged with questions about what he/she knows (knowledge-based), has (possession-based) or is (biometric-based).
Advance-Fee Fraud
Advance-Fee Fraud is a common fraud scheme generally involving a criminal tricking a victim into paying an up-front fee with the promise of a larger reward paid out later.
AI (Artificial Intelligence)
AI or Artificial Intelligence is broadly used to describe the simulation of the processes of human intelligence by computer systems. The processes simulate human learning in that the systems start with the acquisition of information, creating rules for using the information, reasoning by using the rules to reach conclusions, and self-correction by evaluating outcomes and compensating for incorrect predictions or errors. Artificial intelligence is generally categorized into one of three types: 1) Weak AI or Narrow AI, in which the systems and algorithms are trained to perform narrowly focused tasks, 2. Strong AI or General Intelligence, the theoretical goal of having a system apply intelligence to solve any problem much like a human would, and 3) Superintelligence, in which a system could far outperform human intelligence through rapid, recursive self-improvement. Although general intelligence and superintelligence are frequently discussed in media and entertainment, neither has been achieved and neither seems to be achievable in the near future. Artificial intelligence is often used interchangeably (but incorrectly) with machine learning and deep learning. AI is the science and approach to developing technology that mimics human intelligence. Machine learning, a subset of AI, involves the application of statistical techniques and modelling to create algorithms that improve with experience. Deep learning, a subset of machine learning, involves the creation of algorithms using multilayered neural networks trained on vast amounts of data.
AML (Anti-Money Laundering)
Combating Financial Crime: Understanding Anti-Money Laundering (AML)
AML or Anti-Money Laundering refers to a set of procedures, laws, or regulations designed to stop the practice of generating income through illegal activities. 'Money laundering' is the process in which criminals undertake a series of steps that make it look like money made from illegal or unethical activities was earned legitimately and can enter the traditional banking system. Most anti-money laundering programs focus on the source of funds as opposed to anti-terrorism and similar programs which focus on the destination of funds. In modern finance, a typical anti-money laundering program would be run by financial institutions to analyze customer data and detect suspicious transactions.
Did you know?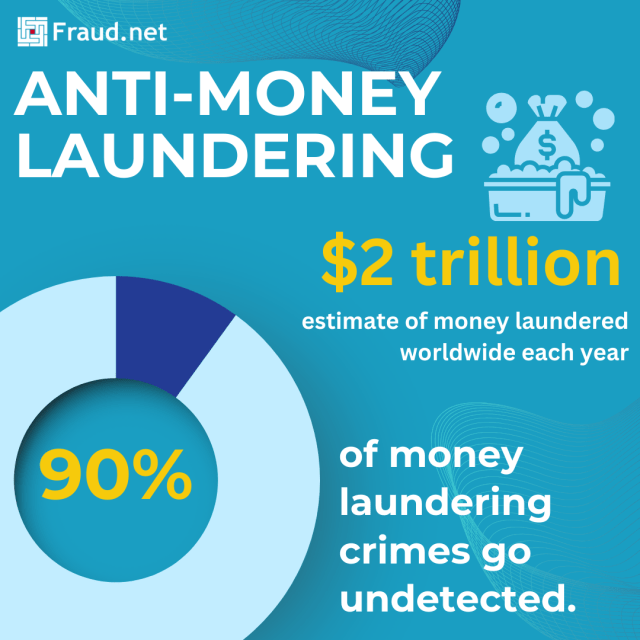
- 300 billion is laundered through the United States each year
- Worldwide, criminals launder between $800 million and $2 trillion each year.
- 90% of money laundering crimes go undetected.
What is AML?
Anti-Money Laundering, commonly known as AML, refers to a set of laws, regulations, and procedures aimed at preventing individuals and organizations from concealing the origins of illegally obtained money. The primary goal of AML is to detect and deter money laundering activities, which typically involve three main stages: placement, layering, and integration. These activities are used to legitimize funds obtained through illegal means, such as drug trafficking, fraud, corruption, or terrorism.
Common Types of Money Laundering:
Money laundering typically consists of three primary stages:
- Placement: Introducing illegal funds into the legitimate financial system.
- Layering: Creating complex layers of transactions to obscure the money's source.
- Integration: Reintroducing laundered funds into the economy, making them appear legitimate.
AML focuses on identifying and preventing these activities by requiring financial institutions to implement safeguards, report suspicious transactions, and maintain comprehensive records.
Six Key AML Solutions
A robust AML program involves a combination of measures that aim to identify, monitor, and report suspicious activities.
The six most popular solutions include:
- Customer Due Diligence (CDD): Verifying the identity of customers and assessing their risk profile.
- Transaction Monitoring: Tracking and analyzing transactions to detect unusual or suspicious behavior.
- Suspicious Activity Reporting: Reporting potential money laundering activities to the appropriate authorities.
- Record-keeping: Maintaining comprehensive records of customer information, transactions, and risk assessments.
- Employee Training: Ensuring that employees are educated and trained to recognize and report suspicious activities.
- Regulatory Compliance: Staying up-to-date with AML laws and regulations to adapt to evolving risks.
Strengthen Your AML Defense with Fraud.net.
Fraud.net is a leading provider of advanced solutions for AML and KYC monitoring. Their platform offers a comprehensive suite of tools to help organizations effectively combat money laundering and other financial crimes and achieve compliance with local regulations.
To learn more about how Fraud.net can tailor a solution to meet your specific AML needs and explore their other capabilities, book a demo and speak with one of our solutions consultants today!
Arbers
In the world of online betting and gambling, an arber is a person who takes advantage of discrepancies in gambling sites odds, so as to ensure that no matter what party wins a contest (i.e. a race), the arber will always win money/cannot lose money. An arber essentially takes advantage of situations where it is mathematically guaranteed they will win money by betting on every single contender of a contest.
AVS (Address Verification System)
AVS or Address Verification System is a payment processing system comparison of the numerical portions of billing and shipping addresses with the addresses on file at the credit card-issuing bank. A single-digit code is returned that represents a match, a partial match, or a number of errors or alerts. The original concept contemplated that the transaction could then be subsequently approved, declined or set aside for manual review. AVS is one of only a few metrics provided to merchants by the issuing banks to assist in the merchants' risk assessment, but AVS responses are also one of the biggest reasons legitimate orders are declined.

