What is Proxy Piercing?
Proxy piercing refers to a technology that enables hosts to determine whether a person is making a proxy purchase or not. A proxy purchase describes a transaction made where a customer disguises their IP via the use of a proxy server.
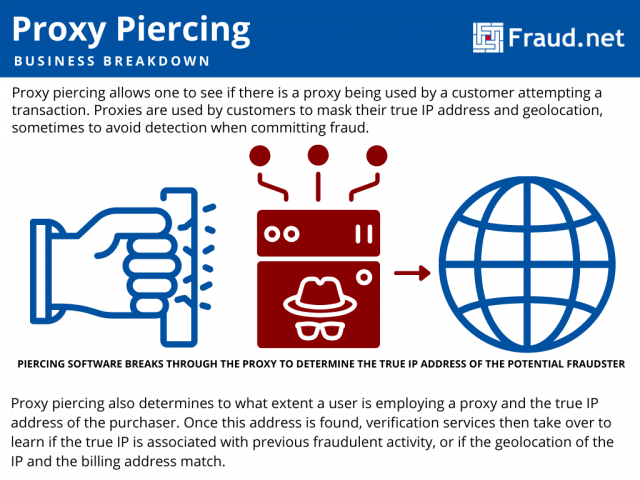
Proxy piercing allows one to see if there is a proxy being used by a customer attempting a transaction. Then, depending on the level of the piercing program, it will “pierce” the proxy server and determine the original IP of the transaction. At an even higher level, proxy piercing can also determine the physical location of that user.
Why is Proxy Piercing Important in Fraud Detection?
Fraudsters often use proxy servers to mask their true identities when making fraudulent purchases or chargebacks. They do this to avoid detection that the address on their payment method does not match their IP address’s geolocation. Proxy piercing cuts through that protective wall, identifying whether a purchaser is using a proxy. It also determines to what extent, and the true IP address of the purchaser.
Once this address is found, verification services then take over. They weigh the true IP address against the location of a purchase’s shipping address or common bank transactions to determine if the purchase is fraudulent. In addition, this IP address can be weighed against the frequency of past transactions and such frequencies in certain locations.
Proxies for Consumers Aren’t Always Bad
Not all purchases using proxies are fraudulent – some consumers use proxies to avoid sharing location and behavior data with browsers. Or, they use them to avoid targeted ads and the sale of their internet behavior and social network data. They may use VPNs to avoid tracking or data spying on public shared networks, like those at cafes or libraries. They may also use proxy servers to avoid government censorship, to access restricted websites in their countries like YouTube or Facebook. Unfortunately, the use of these proxies can open consumers and businesses up to potential phishing or pharming attacks. This vulnerability contributes to fraudsters obtaining credentials they can sell as part of “fullz” packages.
Fraud Detection and Protection with Fraud.net
Through IP verification and Dark Web Monitoring, among other solutions, Fraud.net’s suite of AI-powered fraud detection and protection services can help your institution combat fraudsters.
Weighing IP geolocation data and dark web activity allows for better tracking of fraudulent purchases. Additionally, these services weigh past fraudulent activity against the IPs or credentials in use. Therefore, if a user employs a proxy server to make fraudulent transactions, our services can identify how problematic the true IP is.
Contact us today for recommendations and a demo of our services: